phpMyAdmin provides a web-based interface for managing MySQL and MariaDB databases without memorizing SQL commands. Whether you need to create databases for WordPress sites, manage user permissions for web applications, or export backups before server migrations, phpMyAdmin handles these tasks through an intuitive graphical interface. By the end of this guide, you will have a fully functional phpMyAdmin installation running on the LEMP stack (Linux, Nginx, MariaDB, PHP), secured with SSL encryption from Let’s Encrypt.
Install LEMP Stack on Debian for phpMyAdmin
Each Debian version ships with a different PHP version: Debian 13 (Trixie) includes PHP 8.4, Debian 12 (Bookworm) includes PHP 8.2, and Debian 11 (Bullseye) includes PHP 7.4. The commands in this guide work across all three versions, but you will need to adjust the PHP-FPM socket path in the Nginx configuration to match your PHP version.
Update System Packages
First, update your package lists and upgrade installed packages to ensure a clean starting point:
sudo apt update && sudo apt upgradeAfter the upgrade completes, reboot your system if the kernel was updated before continuing.
Install Nginx Web Server
Next, install Nginx to serve as the web server for phpMyAdmin:
sudo apt install nginxAfter installation completes, verify Nginx is running:
systemctl status nginxExpected output shows Active: active (running):
● nginx.service - A high performance web server and a reverse proxy server
Loaded: loaded (/lib/systemd/system/nginx.service; enabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 10:00:00 UTC; 5s ago
Docs: man:nginx(8)
Process: 1234 ExecStartPre=/usr/sbin/nginx -t -q -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Process: 1235 ExecStart=/usr/sbin/nginx -g daemon on; master_process on; (code=exited, status=0/SUCCESS)
Main PID: 1236 (nginx)
Tasks: 2 (limit: 4651)
Memory: 2.5M
CPU: 15ms
CGroup: /system.slice/nginx.service
├─1236 "nginx: master process /usr/sbin/nginx -g daemon on; master_process on;"
└─1237 "nginx: worker process"
Alternatively, if the service is not active, enable and start it:
sudo systemctl enable nginx --nowBy default, this installs the Nginx version packaged with your Debian release. For a detailed walkthrough of Nginx installation and configuration options, see our guide on installing Nginx on Debian. Alternatively, if you need the latest mainline or stable release from nginx.org, follow our Nginx mainline installation guide for Debian.
Install MariaDB Database Server
After Nginx is running, install MariaDB as the database backend for phpMyAdmin:
sudo apt install mariadb-server mariadb-clientAdditionally, for the latest MariaDB version from official repositories, see our guide on installing MariaDB on Debian.
Once installation completes, verify MariaDB is running:
systemctl status mariadbExpected output shows Active: active (running):
● mariadb.service - MariaDB 10.11.x database server
Loaded: loaded (/lib/systemd/system/mariadb.service; enabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 10:00:00 UTC; 5s ago
Docs: man:mariadbd(8)
https://mariadb.com/kb/en/library/systemd/
Main PID: 2345 (mariadbd)
Status: "Taking your SQL requests now..."
Tasks: 9 (limit: 4651)
Memory: 80.0M
CPU: 500ms
CGroup: /system.slice/mariadb.service
└─2345 /usr/sbin/mariadbd
If MariaDB is not active, enable and start it:
sudo systemctl enable mariadb --nowSecure MariaDB Installation
Following installation, run the security script to set a root password, remove anonymous users, disable remote root login, and delete the test database:
sudo mysql_secure_installationFollow the interactive prompts, answering Y to all questions for maximum security:
NOTE: RUNNING ALL PARTS OF THIS SCRIPT IS RECOMMENDED FOR ALL MariaDB
SERVERS IN PRODUCTION USE! PLEASE READ EACH STEP CAREFULLY!
In order to log into MariaDB to secure it, we'll need the current
password for the root user. If you've just installed MariaDB, and
haven't set the root password yet, you should just press enter here.
Enter current password for root (enter for none):
OK, successfully used password, moving on...
Setting the root password or using the unix_socket ensures that nobody
can log into the MariaDB root user without the proper authorisation.
You already have your root account protected, so you can safely answer 'n'.
Switch to unix_socket authentication [Y/n] Y
Enabled successfully!
Reloading privilege tables..
... Success!
You already have your root account protected, so you can safely answer 'n'.
Change the root password? [Y/n] Y
New password:
Re-enter new password:
Password updated successfully!
Reloading privilege tables..
... Success!
By default, a MariaDB installation has an anonymous user, allowing anyone
to log into MariaDB without having to have a user account created for
them. This is intended only for testing, and to make the installation
go a bit smoother. You should remove them before moving into a
production environment.
Remove anonymous users? [Y/n] Y <---- Type Y then press the ENTER KEY.
... Success!
Normally, root should only be allowed to connect from 'localhost'. This
ensures that someone cannot guess at the root password from the network.
Disallow root login remotely? [Y/n] Y <---- Type Y then press the ENTER KEY.
... Success!
By default, MariaDB comes with a database named 'test' that anyone can
access. This is also intended only for testing, and should be removed
before moving into a production environment.
Remove test database and access to it? [Y/n] Y <---- Type Y then press the ENTER KEY.
- Dropping test database...
... Success!
- Removing privileges on test database...
... Success!
Reloading the privilege tables will ensure that all changes made so far
will take effect immediately.
Reload privilege tables now? [Y/n] Y <---- Type Y then press the ENTER KEY.
... Success!
Cleaning up...
All done! If you've completed all of the above steps, your MariaDB
installation should now be secure.
Thanks for using MariaDB!
Install PHP and Required Extensions
Next, install PHP-FPM and the extensions required by phpMyAdmin. For additional PHP versions or configurations, see our guide on installing PHP on Debian.
sudo apt install php-fpm php-mbstring php-bcmath php-xml php-mysql php-common php-gd php-cli php-curl php-zipAfter installation, verify the PHP-FPM service is running. The command varies by Debian version:
# Debian 13 (Trixie) - PHP 8.4
systemctl status php8.4-fpm
# Debian 12 (Bookworm) - PHP 8.2
systemctl status php8.2-fpm
# Debian 11 (Bullseye) - PHP 7.4
systemctl status php7.4-fpmTo find your installed PHP version, run
php -v. Note your version number as you will need it when configuring the Nginx server block later.
Expected output shows Active: active (running) (example for Debian 12):
● php8.2-fpm.service - The PHP 8.2 FastCGI Process Manager
Loaded: loaded (/lib/systemd/system/php8.2-fpm.service; enabled; preset: enabled)
Active: active (running) since Fri 2024-12-06 10:00:00 UTC; 5s ago
Docs: man:php-fpm8.2(8)
Process: 3456 ExecStartPost=/usr/lib/php/php-fpm-socket-helper install /run/php/php-fpm.sock /etc/php/8.2/fpm/pool.d/www.conf 82 (code=exited, status=0/SUCCESS)
Main PID: 3455 (php-fpm8.2)
Status: "Processes active: 0, idle: 2, Requests: 0, slow: 0, Traffic: 0req/sec"
Tasks: 3 (limit: 4651)
Memory: 9.5M
CPU: 50ms
CGroup: /system.slice/php8.2-fpm.service
├─3455 "php-fpm: master process (/etc/php/8.2/fpm/php-fpm.conf)"
├─3457 "php-fpm: pool www"
└─3458 "php-fpm: pool www"
If PHP-FPM is not active, enable and start it (replace the version number to match your installation):
# Example for Debian 12
sudo systemctl enable php8.2-fpm --nowDownload and Configure phpMyAdmin
With the LEMP stack now installed, proceed to download the latest phpMyAdmin release and configure it to work with Nginx and MariaDB.
While Debian provides a
phpmyadminpackage in its repositories, this guide uses the official tarball method. The Debian package automatically configures Apache integration and creates system files, which requires additional adjustments for Nginx setups. Installing from the official tarball provides direct control over the installation directory, configuration, and version management, making it better suited for custom Nginx deployments.
Create a phpMyAdmin Database User
To begin, create a dedicated superuser for phpMyAdmin instead of using the MariaDB root account. This approach follows the security principle of least privilege.
First, log into the MariaDB shell:
sudo mariadb -u rootOnce connected, create the phpMyAdmin user with a strong password:
Replace
your_secure_passwordwith a strong, unique password. Use a password generator or create one with at least 16 characters including uppercase, lowercase, numbers, and symbols.
CREATE USER 'pmauser'@'localhost' IDENTIFIED BY 'your_secure_password';Next, grant privileges to the user (scoped to all databases with standard privileges, without superuser grant rights):
GRANT SELECT, INSERT, UPDATE, DELETE, CREATE, DROP, INDEX, ALTER, CREATE TEMPORARY TABLES, LOCK TABLES ON *.* TO 'pmauser'@'localhost';Then, apply the privilege changes:
FLUSH PRIVILEGES;Finally, exit the MariaDB shell:
QUIT;Download phpMyAdmin
Now, download the latest phpMyAdmin release directly from the official website. The following script fetches the current version number and downloads the corresponding archive:
DATA="$(wget https://www.phpmyadmin.net/home_page/version.txt -q -O-)"
URL="$(echo $DATA | cut -d ' ' -f 3)"
VERSION="$(echo $DATA | cut -d ' ' -f 1)"
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gzDuring download, you should see output similar to:
--2024-12-06 10:00:00-- https://files.phpmyadmin.net/phpMyAdmin/[version]/phpMyAdmin-[version]-all-languages.tar.gz Resolving files.phpmyadmin.net... [IP address] Connecting to files.phpmyadmin.net|[IP address]|:443... connected. HTTP request sent, awaiting response... 200 OK Length: [bytes] ([size]) [application/x-gzip] Saving to: 'phpMyAdmin-[version]-all-languages.tar.gz' phpMyAdmin-[version] 100%[===================>] [size] [speed] in [time] [date/time] ([speed]) - 'phpMyAdmin-[version]-all-languages.tar.gz' saved [bytes/bytes]
Alternatively, for an English-only version with a smaller file size, use:
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-english.tar.gzVerify Download Integrity
Before extracting, verify the download integrity using SHA256 checksum and PGP signature to ensure the tarball hasn’t been tampered with:
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gz.sha256
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gz.ascFirst, verify the SHA256 checksum:
sha256sum -c phpMyAdmin-${VERSION}-all-languages.tar.gz.sha256Expected output shows OK:
phpMyAdmin-[version]-all-languages.tar.gz: OK
Next, verify the PGP signature. First, import the phpMyAdmin release signing key:
gpg --keyserver hkps://keys.openpgp.org --recv-keys 3D06A59ECE730EB71B511C17CE752F178259BD92Alternatively, download from the phpMyAdmin keyserver:
gpg --keyserver hkps://keyserver.ubuntu.com --recv-keys 3D06A59ECE730EB71B511C17CE752F178259BD92Then verify the signature:
gpg --verify phpMyAdmin-${VERSION}-all-languages.tar.gz.asc phpMyAdmin-${VERSION}-all-languages.tar.gzExpected output includes Good signature (you may see a warning about the key not being certified, which is normal):
gpg: Signature made [date] using RSA key ID 8259BD92 gpg: Good signature from "Isaac Bennetch"
After verifying integrity, extract the archive:
tar xvf phpMyAdmin-${VERSION}-all-languages.tar.gzInstall phpMyAdmin Files
After extraction completes, move the files to the web directory:
sudo mv phpMyAdmin-*/ /var/www/phpmyadminSubsequently, create the temporary directory required by phpMyAdmin:
sudo mkdir /var/www/phpmyadmin/tmpConfigure phpMyAdmin Settings
phpMyAdmin requires a temporary directory for operations like imports and exports. The
$cfg['TempDir']setting must point to a writable directory outside the web root for security.
First, copy the sample configuration file to create your working configuration:
sudo cp /var/www/phpmyadmin/config.sample.inc.php /var/www/phpmyadmin/config.inc.phpAfter that, open the configuration file in a text editor:
sudo nano /var/www/phpmyadmin/config.inc.phpWithin the file, locate the blowfish_secret line and add a 32-character random string for cookie encryption:
$cfg['blowfish_secret'] = ''; /* YOU MUST FILL IN THIS FOR COOKIE AUTH! */To generate a strong secret, use the pwgen utility:
sudo apt install pwgenFollowing installation, generate the secret:
pwgen -s 32 1Once generated, copy the output and paste it between the quotes in the configuration file. Example (generate your own, do not copy this):
UvqAlsvTxRdYIyO8TnlkJsVQaWs2LfgL
Once you add the secret, the line should look like this (use your own generated string):
$cfg['blowfish_secret'] = 'UvqAlsvTxRdYIyO8TnlkJsVQaWs2LfgL'; /* YOU MUST FILL IN THIS FOR COOKIE AUTH! */Additionally, configure the temporary directory path by adding this line after the blowfish_secret:
$cfg['TempDir'] = '/var/www/phpmyadmin/tmp';Furthermore, if your database server runs on a different machine, update the host setting to match your server’s IP address:
$cfg['Servers'][$i]['host'] = '192.168.55.101';Set File Permissions
Finally, before configuring Nginx, set ownership to the web server user and configure secure file permissions:
sudo chown -R www-data:www-data /var/www/phpmyadmin/
sudo find /var/www/phpmyadmin/ -type d -exec chmod 755 {} \;
sudo find /var/www/phpmyadmin/ -type f -exec chmod 644 {} \;Create Nginx Server Block for phpMyAdmin
At this point, configure Nginx to serve phpMyAdmin. Using a dedicated subdomain (like pma.example.com) adds security by making the URL less predictable to attackers.
Create the Server Block File
To begin, create a new Nginx configuration file:
sudo nano /etc/nginx/sites-available/phpmyadmin.confAdd the Server Configuration
Now, add the following configuration, replacing pma.example.com with your actual domain:
Adjust the PHP-FPM socket path to match your Debian version: use
php8.4-fpm.sockfor Debian 13,php8.2-fpm.sockfor Debian 12, orphp7.4-fpm.sockfor Debian 11.
server {
listen 80;
listen [::]:80;
server_name pma.example.com;
root /var/www/phpmyadmin/;
index index.php index.html index.htm index.nginx-debian.html;
access_log /var/log/nginx/phpmyadmin_access.log;
error_log /var/log/nginx/phpmyadmin_error.log;
location / {
try_files $uri $uri/ /index.php;
}
location ~ ^/(doc|sql|setup)/ {
deny all;
}
location ~ \.php$ {
fastcgi_pass unix:/run/php/php8.2-fpm.sock;
include snippets/fastcgi-php.conf;
}
location ~ /\.ht {
deny all;
}
}Key configuration notes:
- PHP-FPM socket: The path
/run/php/php8.2-fpm.sockmust match your PHP version. Runls /run/php/to find your socket file. - Document root: The
root /var/www/phpmyadmin/;path matches where you extracted phpMyAdmin earlier.
Furthermore, for additional security, restrict access to specific IP addresses by adding these lines inside the server block (before the location blocks):
allow <your ip address>;
deny all;Consequently, this blocks all access except from your IP address, returning a 403 Forbidden error to others. Place these directives at the server level, before any location blocks.
When finished editing, save the file with CTRL+O and exit with CTRL+X.
Enable the Server Block
Following this, create a symbolic link to enable it:
sudo ln -s /etc/nginx/sites-available/phpmyadmin.conf /etc/nginx/sites-enabled/Test and Apply Configuration
Before restarting Nginx, test the configuration for syntax errors:
sudo nginx -tSubsequently, the expected output should appear:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
After verification completes, restart Nginx to apply the changes:
sudo systemctl restart nginxAccess the phpMyAdmin Web Interface
At this stage, open your web browser and navigate to your phpMyAdmin URL (e.g., http://pma.example.com or http://your-server-ip/phpmyadmin).
Upon loading, the login screen appears:
Subsequently, log in with the database user you created earlier (pmauser). Once logged in, explore the dashboard features.
Explore the Dashboard Features
The Status page provides real-time information about your database server’s health and performance:
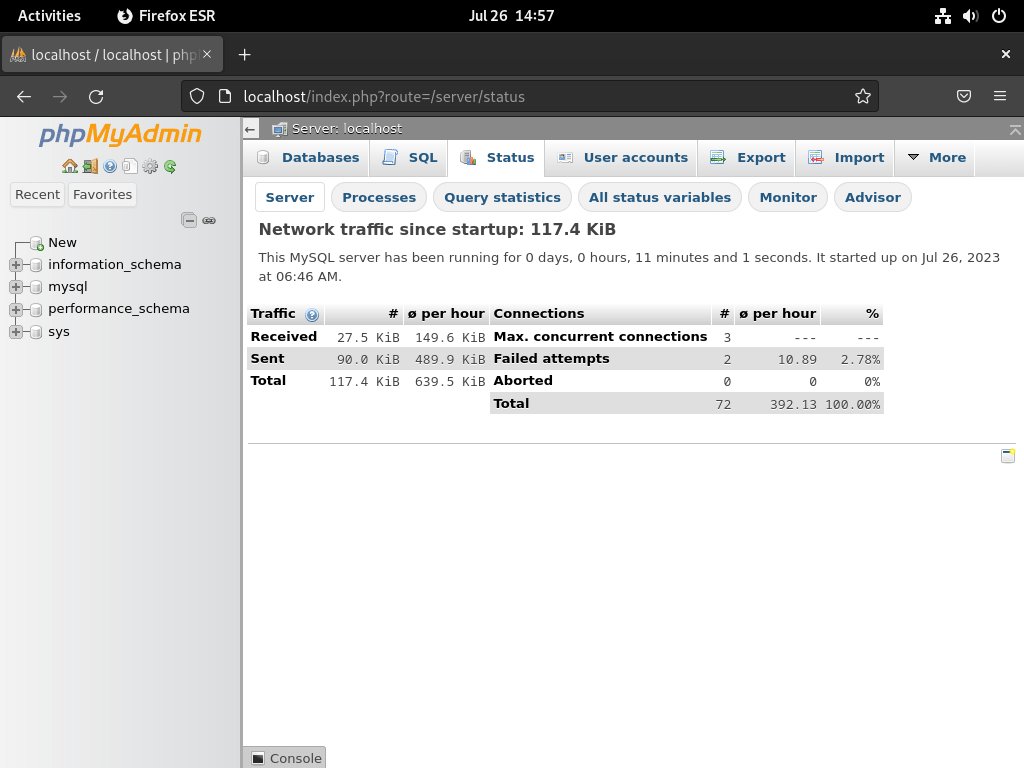
The Advisor system analyzes your database activity and provides optimization recommendations:
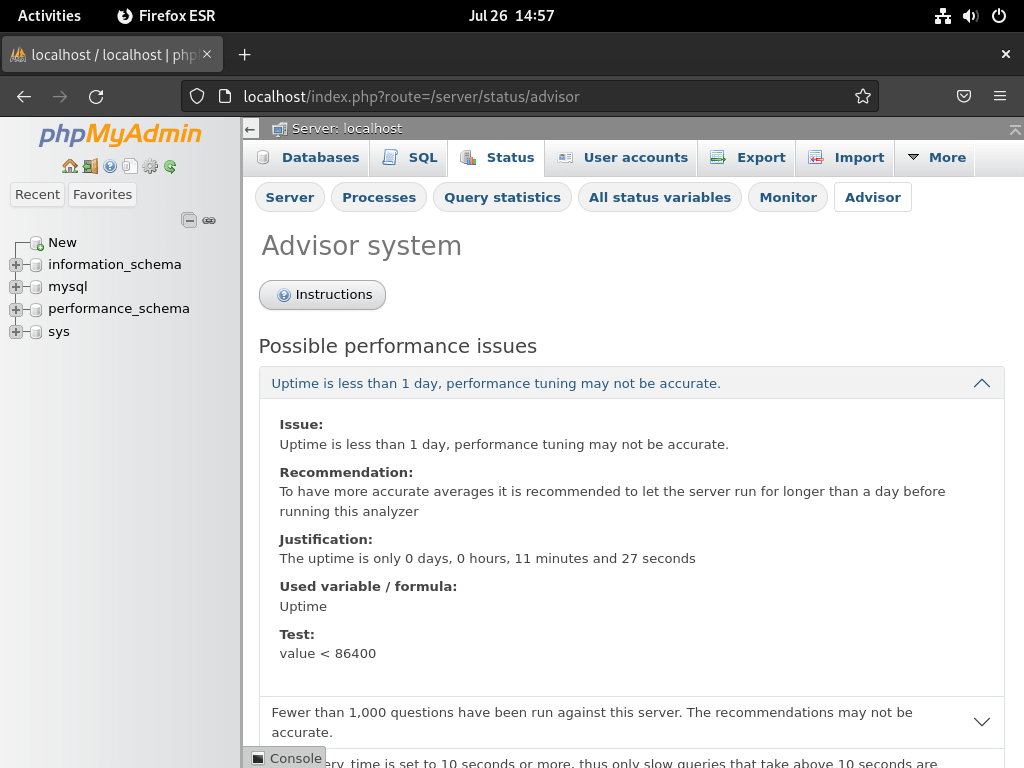
The advisor requires at least 72 hours of database activity to provide accurate recommendations. Test any suggested changes in a staging environment before applying them to production.
The Monitor page displays live graphs of database activity:
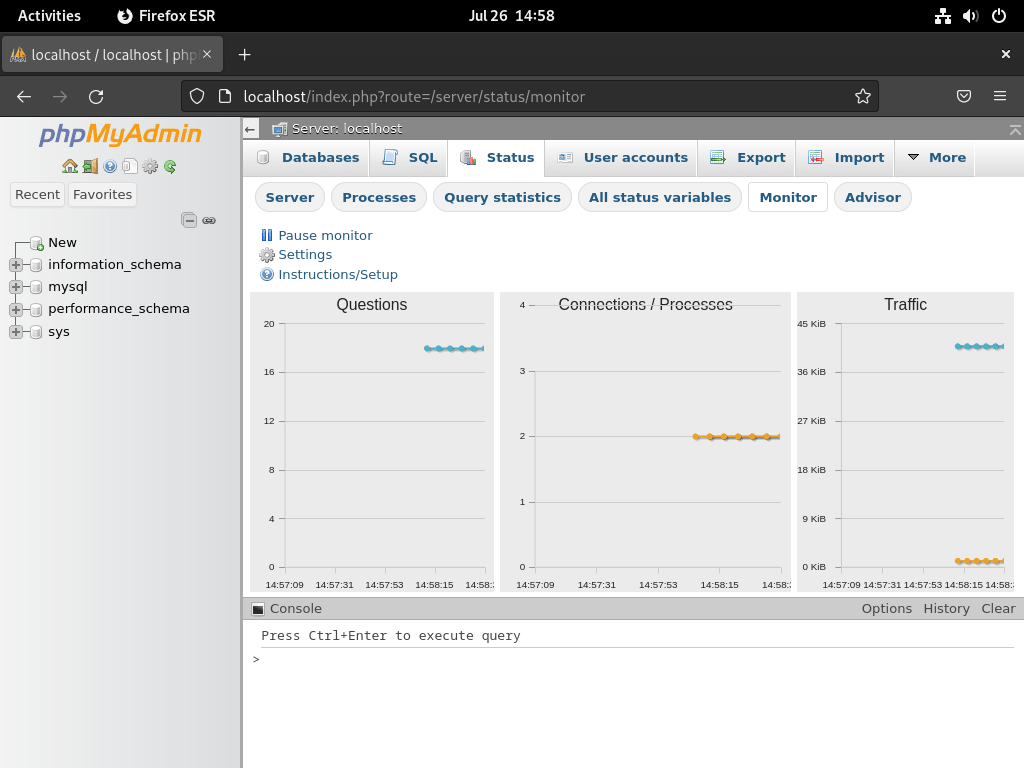
Troubleshooting Common phpMyAdmin Issues
If phpMyAdmin does not load correctly or displays errors, the following troubleshooting steps address the most common issues.
PHP Files Download Instead of Execute (MIME Type Errors)
When your browser downloads PHP files or shows MIME type errors in the console, Nginx is serving PHP files as plain text instead of processing them through PHP-FPM.
First, verify PHP-FPM is running for your PHP version:
# Check your PHP version first
php -v
# Then check the corresponding PHP-FPM service
# Debian 13 (PHP 8.4)
systemctl status php8.4-fpm
# Debian 12 (PHP 8.2)
systemctl status php8.2-fpm
# Debian 11 (PHP 7.4)
systemctl status php7.4-fpmExpected output shows Active: active (running). If the service is not running, start it:
# Replace version number to match your installation
sudo systemctl start php8.2-fpmNext, verify the socket path in your Nginx configuration matches your PHP version:
# List available PHP-FPM sockets
ls -la /run/php/
# Check what your Nginx config uses
grep fastcgi_pass /etc/nginx/sites-available/phpmyadmin.confThe socket path in your Nginx config must match an existing socket file. If you have PHP 8.2 but your config references php7.4-fpm.sock, update the Nginx configuration to use the correct socket:
sudo nano /etc/nginx/sites-available/phpmyadmin.confUpdate the fastcgi_pass line to match your PHP version:
fastcgi_pass unix:/run/php/php8.2-fpm.sock;After making changes, test the configuration and restart Nginx:
sudo nginx -t
sudo systemctl restart nginxAlternative: Using TCP Socket Instead of Unix Socket
If you continue experiencing socket permission issues (particularly on embedded systems like Raspberry Pi OS), switch to TCP sockets as an alternative to Unix sockets.
First, configure PHP-FPM to listen on a TCP port. Edit the PHP-FPM pool configuration:
# Replace version number to match your PHP installation
sudo nano /etc/php/8.2/fpm/pool.d/www.confFind the listen directive and change it from the Unix socket to a TCP address:
; Change from:
; listen = /run/php/php8.2-fpm.sock
; To:
listen = 127.0.0.1:9000Next, update your Nginx configuration to use the TCP socket:
sudo nano /etc/nginx/sites-available/phpmyadmin.confChange the fastcgi_pass directive:
fastcgi_pass 127.0.0.1:9000;Finally, restart both PHP-FPM and Nginx:
# Replace version number to match your installation
sudo systemctl restart php8.2-fpm
sudo systemctl restart nginxUnix sockets offer better performance on standard Debian servers. TCP sockets are primarily useful for troubleshooting permission issues or when running PHP-FPM on embedded systems where socket permissions behave differently.
Blank Page or 502 Bad Gateway Error
A blank page or 502 error indicates Nginx cannot communicate with PHP-FPM. Check the Nginx error log for specific details:
sudo tail -f /var/log/nginx/phpmyadmin_error.logCommon errors include:
connect() to unix:/run/php/phpX.X-fpm.sock failed (2: No such file or directory)– Wrong socket path in Nginx configconnect() to unix:/run/php/phpX.X-fpm.sock failed (13: Permission denied)– Socket permission issueupstream timed out– PHP-FPM not responding, check service status
For socket permission errors, verify the www-data user can access the socket:
# Check socket permissions
ls -la /run/php/
# Socket should be owned by www-data or have appropriate permissions
# Example output:
# srw-rw---- 1 www-data www-data 0 Dec 6 10:00 php8.2-fpm.sockCannot Log In or Authentication Errors
If phpMyAdmin loads but login fails, verify your database credentials and user permissions. Test the database connection directly:
# Test connection with the phpMyAdmin user
mariadb -u pmauser -pIf the command-line connection succeeds but phpMyAdmin still fails, check the phpMyAdmin configuration file for the correct host setting:
grep "host" /var/www/phpmyadmin/config.inc.phpFor local databases, this should show localhost. For remote databases, verify the IP address matches your database server.
Secure phpMyAdmin with Let’s Encrypt SSL
Moving forward, to protect your database credentials in transit, enable HTTPS encryption using a free SSL certificate from Let’s Encrypt. For a detailed guide on Nginx SSL configuration, see our Let’s Encrypt SSL guide for Nginx on Debian.
Install Certbot and Obtain Certificate
To start, install the Certbot Nginx plugin:
sudo apt install python3-certbot-nginx -ySubsequently, obtain and install the certificate (replace with your email and domain):
sudo certbot --nginx --agree-tos --redirect --hsts --staple-ocsp --email you@example.com -d pma.example.comThis command automatically:
- Obtains an SSL certificate from Let’s Encrypt
- Configures Nginx to use HTTPS
- Enables HTTP to HTTPS redirect
- Adds security headers (HSTS, OCSP stapling)
As a result, your phpMyAdmin URL now uses HTTPS: https://pma.example.com
Verify Automatic Certificate Renewal
By default, Certbot installs a systemd timer that automatically renews certificates before they expire. To ensure automatic renewal is configured, verify the timer is active:
sudo systemctl status certbot.timerIn addition, test the renewal process without making changes:
sudo certbot renew --dry-runUltimately, when the dry run succeeds, your certificates will renew automatically without intervention.
Configure UFW Firewall
Additionally, if UFW is enabled on your server, open ports 80 and 443 for web traffic. For a complete UFW setup guide, see installing UFW on Debian.
If connected via SSH, allow SSH access before enabling UFW to avoid being locked out of your server.
sudo ufw allow OpenSSH
sudo ufw allow 'Nginx Full'
sudo ufw enableFollowing this, verify the firewall status:
sudo ufw statusStatus: active To Action From -- ------ ---- OpenSSH ALLOW Anywhere Nginx Full ALLOW Anywhere OpenSSH (v6) ALLOW Anywhere (v6) Nginx Full (v6) ALLOW Anywhere (v6)
Troubleshoot Common phpMyAdmin Issues
502 Bad Gateway Error
This error indicates Nginx cannot connect to PHP-FPM. To diagnose the issue, first check the Nginx error log for details:
sudo tail -5 /var/log/nginx/phpmyadmin_error.logGenerally, a socket mismatch error looks like:
connect() to unix:/run/php/php8.2-fpm.sock failed (2: No such file or directory)
To fix this issue, verify which socket files exist on your system:
ls /run/php/As expected, the output should display your PHP version’s socket:
php8.2-fpm.pid php8.2-fpm.sock
After identification, update the fastcgi_pass line in /etc/nginx/sites-available/phpmyadmin.conf to match your socket file, then restart both services:
sudo systemctl restart php8.2-fpm nginxAccess Denied for User
When you encounter login issues with your phpMyAdmin user, first verify the user exists and has the correct privileges:
sudo mariadb -u root -e "SELECT User, Host FROM mysql.user;"Normally, the pmauser should appear in the output:
+-------------+-----------+ | User | Host | +-------------+-----------+ | mariadb.sys | localhost | | mysql | localhost | | pmauser | localhost | | root | localhost | +-------------+-----------+
However, if the user is missing from the list, recreate it following the database user creation steps above.
Blowfish Secret Error
When you encounter “The configuration file now needs a secret passphrase,” the blowfish_secret value is empty or too short. To resolve this, generate a new 32-character secret:
pwgen -s 32 1Afterward, add this to /var/www/phpmyadmin/config.inc.php in the blowfish_secret setting.
Permission Denied Errors
Should phpMyAdmin display permission errors, reset the ownership and permissions:
sudo chown -R www-data:www-data /var/www/phpmyadmin/
sudo find /var/www/phpmyadmin/ -type d -exec chmod 755 {} \;
sudo find /var/www/phpmyadmin/ -type f -exec chmod 644 {} \;Update phpMyAdmin
Over time, to keep phpMyAdmin secure and current, download the new release and replace the existing files:
Warning: The following update process will delete the existing phpMyAdmin directory. Back up your
config.inc.phpfile before proceeding to preserve your settings.
# Download latest version
DATA="$(wget https://www.phpmyadmin.net/home_page/version.txt -q -O-)"
VERSION="$(echo $DATA | cut -d ' ' -f 1)"
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gz
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gz.sha256
wget https://files.phpmyadmin.net/phpMyAdmin/${VERSION}/phpMyAdmin-${VERSION}-all-languages.tar.gz.asc
# Verify integrity
sha256sum -c phpMyAdmin-${VERSION}-all-languages.tar.gz.sha256
gpg --verify phpMyAdmin-${VERSION}-all-languages.tar.gz.asc phpMyAdmin-${VERSION}-all-languages.tar.gz
# Backup existing configuration
sudo cp /var/www/phpmyadmin/config.inc.php ~/phpmyadmin-config.inc.php.backup
# Extract and replace
tar xvf phpMyAdmin-${VERSION}-all-languages.tar.gz
sudo rm -rf /var/www/phpmyadmin
sudo mv phpMyAdmin-${VERSION}-all-languages /var/www/phpmyadmin
# Restore configuration
sudo cp ~/phpmyadmin-config.inc.php.backup /var/www/phpmyadmin/config.inc.php
sudo mkdir /var/www/phpmyadmin/tmp
# Reset permissions
sudo chown -R www-data:www-data /var/www/phpmyadmin/
sudo find /var/www/phpmyadmin/ -type d -exec chmod 755 {} \;
sudo find /var/www/phpmyadmin/ -type f -exec chmod 644 {} \;
# Reload services
sudo systemctl reload php8.2-fpm
sudo systemctl reload nginxThe backup and restore process preserves your
blowfish_secret, database host configuration, andTempDirsetting. However, always verify the configuration file syntax after restoring.
Remove phpMyAdmin
Alternatively, if you no longer need phpMyAdmin, follow these steps to completely remove it from your system:
Remove phpMyAdmin Files
Warning: The following command permanently deletes phpMyAdmin and all its configuration files. Ensure you have backed up any custom configurations before proceeding.
sudo rm -rf /var/www/phpmyadminRemove Nginx Server Block
Following that, remove the Nginx configuration files:
sudo rm /etc/nginx/sites-enabled/phpmyadmin.conf
sudo rm /etc/nginx/sites-available/phpmyadmin.conf
sudo systemctl restart nginxRemove Database User (Optional)
Additionally, for complete cleanup, remove the phpMyAdmin database user if you no longer need it:
sudo mariadb -u root -e "DROP USER 'pmauser'@'localhost'; FLUSH PRIVILEGES;"Remove LEMP Stack (Optional)
Lastly, if you want to remove the entire LEMP stack:
Warning: These commands remove Nginx, MariaDB, and PHP along with all databases and website files. Only proceed if you no longer need any web services on this server.
sudo apt remove --purge nginx mariadb-server mariadb-client php-fpm php-* -y
sudo apt autoremove -yConclusion
At this point, you now have phpMyAdmin running on Debian with Nginx, secured by Let’s Encrypt SSL. The web interface simplifies database administration tasks like creating tables, managing users, importing SQL files, and exporting backups. For production deployments, however, consider restricting access by IP address in your Nginx configuration and implementing regular database backups using MariaDB’s mysqldump utility.



Thanks for a flawlessly working tutorial, but ….
at starting (with an empty screen) of phpmyadmin using Google developer tools I found problems with
Refused to execute script from because its MIME type (…) and strict MIME type (…)
file not founnd
autoload
I changed the setup as follows
moved php,yadmin to a subfolder of /var/www/
deleted phpmyadmin.conf
use 127.0.0.1:9000 instead of php8.2-fpm.sock
in /etc/nginx/sites_enabled/mylocal and in /etc/php/8.2/fpm/pool.d/www.conf
I did the setup on a fresh installed Raspberry Pi OS 64 bit for a Raspberry Pi 3B+
All is working fine now.
Thanks for sharing your setup and the detailed troubleshooting, Michael. The MIME type warnings you encountered back in August typically point to PHP-FPM not executing files properly. Your solution switching to TCP socket 127.0.0.1:9000 makes perfect sense for Raspberry Pi OS, where Unix socket permissions can behave differently than standard Debian.
The guide assumes standard Debian server environments where Unix sockets offer better performance, but TCP sockets are absolutely valid for embedded systems or when debugging permission issues. Good instincts moving phpMyAdmin to a subfolder and testing with different socket configurations until it worked.