This guide walks you through how to install PuTTY SSH on Debian, covering both the APT package manager and Flatpak methods. PuTTY provides a graphical SSH client for connecting to remote servers, transferring files with PSCP, and managing multiple saved sessions. By the end, you will have PuTTY configured with saved sessions, key-based authentication, and PSCP ready for secure file transfers.
Install PuTTY SSH on Debian
PuTTY is available through Debian’s default repositories and as a Flatpak from Flathub. Each method offers different advantages depending on your needs.
| Method | Channel | Version | Updates | Best For |
|---|---|---|---|---|
| APT Package Manager | Debian Repos | Distribution default | Automatic via apt upgrade | Most users who prefer distro-tested packages |
| Flatpak | Flathub | Latest stable | Automatic via flatpak update | Users who want the newest features with sandboxing |
For most users, the APT method is recommended because it integrates with your system’s package management and receives security updates through standard Debian channels. Alternatively, choose Flatpak if you prefer sandboxed applications or want consistent versions across different Linux distributions.
Update Debian Before PuTTY Installation
Before installing any packages, update your system to ensure you have the latest security patches and package lists:
sudo apt update && sudo apt upgradeThis command requires
sudoprivileges. If your user account is not in thesudogroup, see our guide on adding a user to sudoers on Debian.
Install PuTTY via APT Package Manager
Debian includes PuTTY in its default repositories, so installation requires just a single command. Install both the graphical client and command-line tools:
sudo apt install putty putty-toolsThe putty package provides the graphical SSH client, while putty-tools includes command-line utilities like PSCP (secure file copy), PSFTP (secure file transfer), and PuTTYgen (key generator).
Verify PuTTY Installation on Debian
After installation completes, verify the setup using the PSCP command-line tool, which works in both desktop and headless environments:
pscp --versionpscp: Release 0.83 Build platform: 64-bit Unix Compiler: gcc 14.2.0 Source commit: d2c178c49a0ae6fa9ef75ca84fb3c9d0d675ea85
| Debian Release | PuTTY Version |
|---|---|
| Debian 13 (Trixie) | 0.83.x |
| Debian 12 (Bookworm) | 0.78.x |
| Debian 11 (Bullseye) | 0.74.x |
All versions provide the core SSH functionality covered in this guide. The output above reflects Debian 13; older releases show different version numbers and compiler details.
Install PuTTY via Flatpak
As an alternative, Flatpak provides the latest PuTTY release with sandboxing for enhanced security. If Flatpak is not installed on your system, see our guide on installing Flatpak on Debian before continuing.
Add the Flathub repository if you haven’t already:
sudo flatpak remote-add --system --if-not-exists flathub https://dl.flathub.org/repo/flathub.flatpakrepoInstall PuTTY from Flathub:
sudo flatpak install --system flathub uk.org.greenend.chiark.sgtatham.puttyVerify the installation:
flatpak list | grep -i puttyPuTTY uk.org.greenend.chiark.sgtatham.putty 0.83 stable flathub
Launch the Flatpak version from the terminal:
flatpak run uk.org.greenend.chiark.sgtatham.puttyThe Flatpak version runs in a sandbox with limited filesystem access. To transfer files with PSCP, you may need to grant additional permissions or use the APT installation instead.
Launch PuTTY on Debian
Launch PuTTY from the terminal:
puttyOnce launched, the PuTTY Configuration window appears, ready for you to enter connection details or load a saved session.
Alternatively, you can launch PuTTY from your desktop environment’s applications menu. Simply search for “PuTTY” in your applications launcher and click the PuTTY SSH Client icon.
The exact menu location varies by desktop environment. GNOME users find it under Activities → Show Applications. KDE, XFCE, and other desktops have their own application launchers.
Getting Started with PuTTY on Debian
Now that PuTTY is installed, this section covers essential features for managing remote connections effectively.
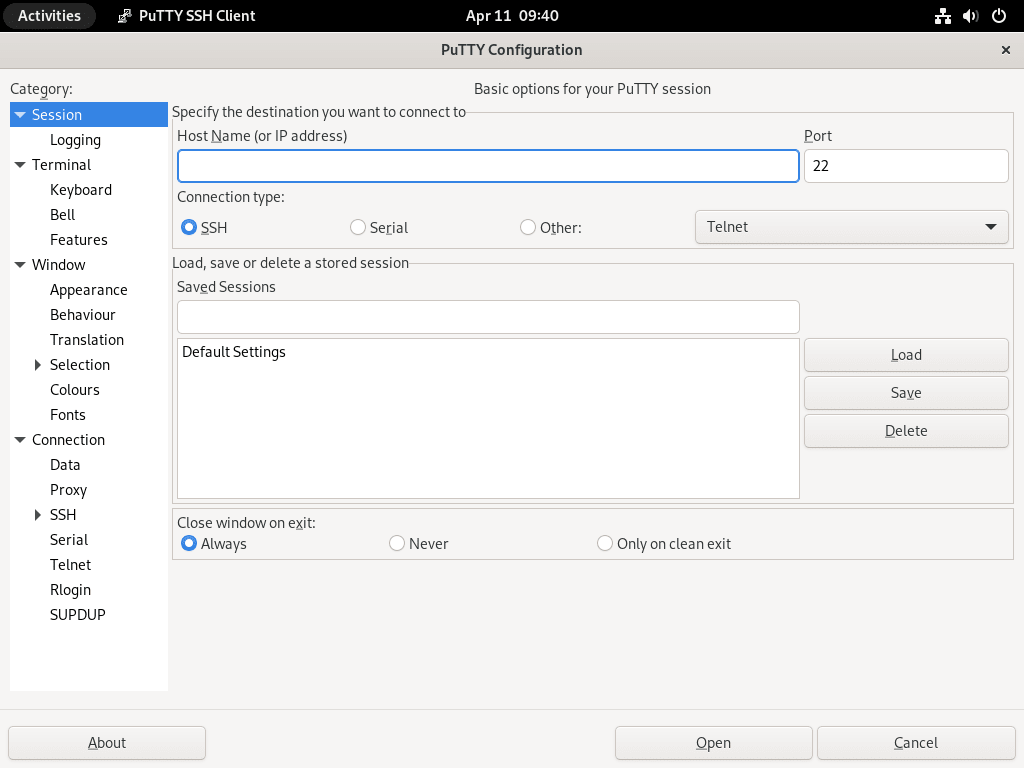
Configure and Save PuTTY SSH Sessions
One of the key features of PuTTY is the ability to save and manage multiple SSH sessions. To configure and save a new SSH session, follow these steps:
- Launch PuTTY.
- In the Session category, enter the remote server’s hostname or IP address in the Host Name (or IP address) field.
- Specify the port number in the Port field (default is 22 for SSH).
- Choose SSH as the connection type.
- Enter a descriptive name for the session in the Saved Sessions field and click the Save button.
After you have saved a session, you can quickly load its settings by selecting it from the Saved Sessions list and clicking Load.
Customize PuTTY’s Appearance
Beyond basic connections, PuTTY allows you to customize its appearance to suit your preferences. Some common customizations include:
- Changing the font and size: Navigate to Window > Appearance. Click the Change button next to the Font settings section to choose a different font and size.
- Adjusting window colors: Go to Window > Colours. Select the color you want to change and click the Modify button to choose a new color.
- Setting window transparency: Navigate to Window > Behaviour. Enable the system-provided window decorations (if available) option, and adjust the window transparency slider.
Use Key-Based Authentication with PuTTY
Key-based authentication is a more secure method of logging into remote servers than passwords. PuTTYgen generates keys in PuTTY’s native .ppk format. For background on how SSH commands work on Linux, see our reference guide.
Generate the key pair:
Ensure the .ssh directory exists:
mkdir -p ~/.ssh && chmod 700 ~/.sshGenerate an Ed25519 key pair:
puttygen -t ed25519 -o ~/.ssh/putty-key.ppkWhen prompted, enter a passphrase to protect the private key (recommended for security). Export the public key in OpenSSH format:
puttygen -L ~/.ssh/putty-key.ppk > ~/.ssh/putty-key.pubVerify the public key was exported correctly:
cat ~/.ssh/putty-key.pubssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAI... user@hostname
Copy the public key to the remote server:
ssh-copy-id -i ~/.ssh/putty-key.pub user@remote-serverIf ssh-copy-id is unavailable, manually append the key:
cat ~/.ssh/putty-key.pub | ssh user@remote-server "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"Configure PuTTY to use the key:
- Launch PuTTY and load or create a session.
- Navigate to Connection > SSH > Auth > Credentials.
- In the “Private key file for authentication” field, browse to your
~/.ssh/putty-key.ppkfile. - Return to the Session category and save your session.
Ed25519 keys offer the best security and performance. RSA (4096-bit) is an alternative if you need compatibility with older servers that don’t support Ed25519.
Enable X11 Forwarding on PuTTY
X11 forwarding allows graphical applications from a remote server to display on your local machine. This requires configuration on both the server and client.
Server-side requirements:
Ensure the remote server allows X11 forwarding. Verify that X11Forwarding yes is set in the SSH configuration:
grep -i x11forwarding /etc/ssh/sshd_configX11Forwarding yes
If the output shows no or the line is missing, edit the configuration and restart SSH:
sudo sed -i 's/^#*X11Forwarding.*/X11Forwarding yes/' /etc/ssh/sshd_config
sudo systemctl restart sshAdditionally, install xauth on the server if it’s missing:
sudo apt install xauthClient-side configuration in PuTTY:
- Launch PuTTY and load or create a session.
- Navigate to Connection > SSH > X11.
- Check Enable X11 forwarding.
- Save the session and connect to the remote server.
Verify X11 forwarding works:
After connecting, check that the DISPLAY variable is set:
echo $DISPLAYlocalhost:10.0
Test with a graphical application:
xeyesIf xeyes is not installed, install it with sudo apt install x11-apps. A window with animated eyes should appear on your local display.
On a Linux desktop, your existing X server (or Wayland with XWayland) handles the display automatically. If connecting from Windows, you need an X server like VcXsrv or Xming installed before X11 forwarding will work.
Transfer Files with PSCP on Debian
PSCP (PuTTY Secure Copy) transfers files securely between your local machine and remote servers using SCP or SFTP protocols. It supports both password and key-based authentication.
Basic File Transfers
Upload a file to a remote server:
pscp local-file.txt user@remote-server:/path/to/destinationThe above command uploads local-file.txt from your local machine to the specified destination path on the remote server.
Download a file from a remote server:
pscp user@remote-server:/path/to/remote-file.txt local-destinationHere, PSCP downloads remote-file.txt from the remote server and saves it to your specified local destination.
Transfer a directory and its contents:
pscp -r local-directory user@remote-server:/path/to/destinationThe -r flag enables recursive mode, uploading the entire directory and its contents to the remote server.
Transfer files using key-based authentication:
pscp -i private-key.ppk local-file.txt user@remote-server:/path/to/destinationWith the -i flag, you can specify a private key file (.ppk) for key-based authentication instead of entering a password.
Advanced PSCP Options
Transfer files over a specific port:
pscp -P 2222 local-file.txt user@remote-server:/path/to/destinationThe -P flag specifies a custom port number, which is useful when servers run SSH on non-standard ports like 2222.
Transfer files using SCP protocol:
pscp -scp local-file.txt user@remote-server:/path/to/destinationThe -scp flag forces PSCP to use the older SCP protocol instead of SFTP.
Transfer files using SFTP protocol:
pscp -sftp local-file.txt user@remote-server:/path/to/destinationThe -sftp flag explicitly enforces SFTP, which provides better error handling and supports more features than SCP.
Display progress while transferring files:
pscp -v local-file.txt user@remote-server:/path/to/destinationFor troubleshooting or monitoring large transfers, add the -v (verbose) flag to display detailed progress information during the transfer.
These PSCP commands cover the most common file transfer scenarios between your local machine and remote servers.
Troubleshoot PuTTY Issues on Debian
Connection Refused
Error message:
Network error: Connection refused
Diagnose: Check if SSH is running on the remote server:
sudo systemctl status sshIf SSH is running, you should see:
● ssh.service - OpenBSD Secure Shell server
Loaded: loaded (/lib/systemd/system/ssh.service; enabled)
Active: active (running) since Thu 2025-12-05 10:00:00 UTC
Fix: If the service is inactive, start and enable it:
sudo systemctl enable --now sshAdditionally, check if the firewall blocks port 22:
sudo ufw statusStatus: active To Action From -- ------ ---- 22/tcp ALLOW Anywhere
If SSH is not listed, allow it with:
sudo ufw allow sshFor more details, see our guide on configuring UFW on Debian.
Host Key Verification Warning
PuTTY displays a security alert the first time you connect to a server. This is normal behavior. Verify the fingerprint matches your server’s key, then click Accept to save the key and continue.
However, if you see this warning for a server you’ve connected to before, the server’s key may have changed due to reinstallation or IP address reuse. In that case, verify with your server administrator before accepting the new key.
Permission Denied (publickey)
Error message:
Disconnected: No supported authentication methods available (server sent: publickey)
Diagnose: This error occurs when key-based authentication fails. Check the following on the remote server:
ls -la ~/.ssh/drwx------ 2 user user 4096 Dec 5 10:00 . -rw------- 1 user user 738 Dec 5 10:00 authorized_keys
Fix: Ensure correct permissions on the server. For a deeper look at file permissions, see our chmod command guide:
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keysAlso verify that:
- The private key file (.ppk) is correctly specified in Connection > SSH > Auth > Credentials
- The corresponding public key exists in
~/.ssh/authorized_keyson the remote server - The public key was exported in OpenSSH format (use
puttygen -L keyfile.ppkto verify)
Verify: Test the connection again after fixing permissions. A successful connection proceeds without password prompts.
Remove PuTTY from Debian
If you no longer need PuTTY, remove it using the method matching your installation.
Remove APT Installation
sudo apt remove putty putty-toolsAfterward, remove orphaned dependencies:
sudo apt autoremoveVerify removal:
pscp --versionbash: pscp: command not found
Remove Flatpak Installation
sudo flatpak uninstall uk.org.greenend.chiark.sgtatham.puttyTo also remove application data stored by Flatpak:
sudo flatpak uninstall --delete-data uk.org.greenend.chiark.sgtatham.puttyVerify the Flatpak was removed:
flatpak list | grep -i puttyNo output confirms successful removal.
Additionally, your PuTTY session configurations may be stored in ~/.putty/ and remain after uninstallation. Back up this directory first if you want to preserve your settings:
cp -r ~/.putty ~/putty-backupThe following command permanently deletes your saved PuTTY sessions, host keys, and preferences. Only run this if you want a complete removal and have backed up any settings you need.
rm -rf ~/.puttyFrequently Asked Questions
Yes. Debian includes PuTTY in its default repositories across all supported releases. Install it with sudo apt install putty putty-tools without adding any third-party sources.
PuTTY provides a graphical interface for SSH connections, session saving, and key management using its own .ppk key format. OpenSSH is command-line only and uses standard OpenSSH key files. PuTTY is often preferred when managing multiple saved sessions or when migrating from Windows, while OpenSSH is the default choice for terminal-based workflows.
Yes. PuTTY 0.68 and later support Ed25519 keys. Generate one with puttygen -t ed25519 -o keyfile.ppk and export the public key in OpenSSH format with puttygen -L keyfile.ppk.
Conclusion
You now have PuTTY installed on Debian with saved SSH sessions, Ed25519 key-based authentication, PSCP file transfers, and X11 forwarding configured. For production servers, consider installing Fail2ban on Debian to protect against brute-force attacks, and review our guide on enabling SSH on Debian for server-side hardening.



Formatting tips for your comment
You can use basic HTML to format your comment. Useful tags currently allowed:
<code>command</code>command<strong>bold</strong><em>italic</em><blockquote>quote</blockquote>